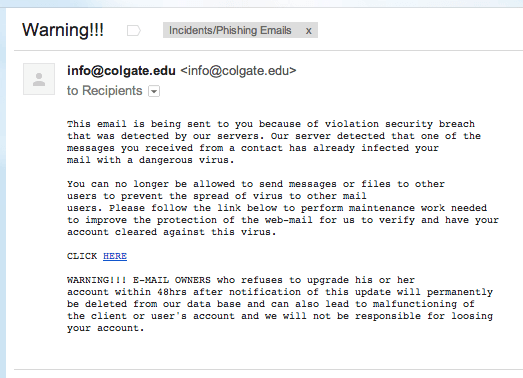
Phishing Incident Report Template

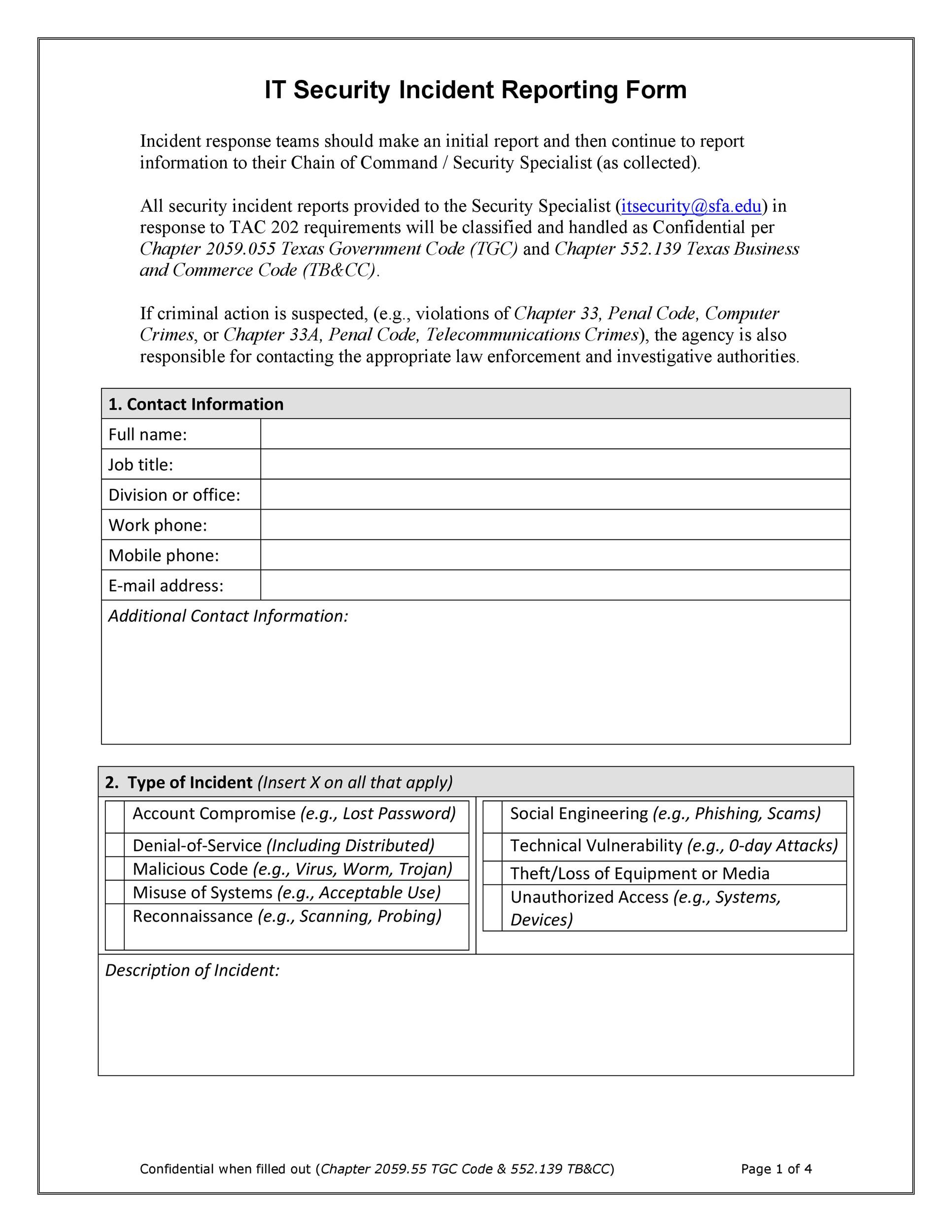
The security incident phishing template allows you to perform a series of tasks designed to handle spear phishing emails on your network.
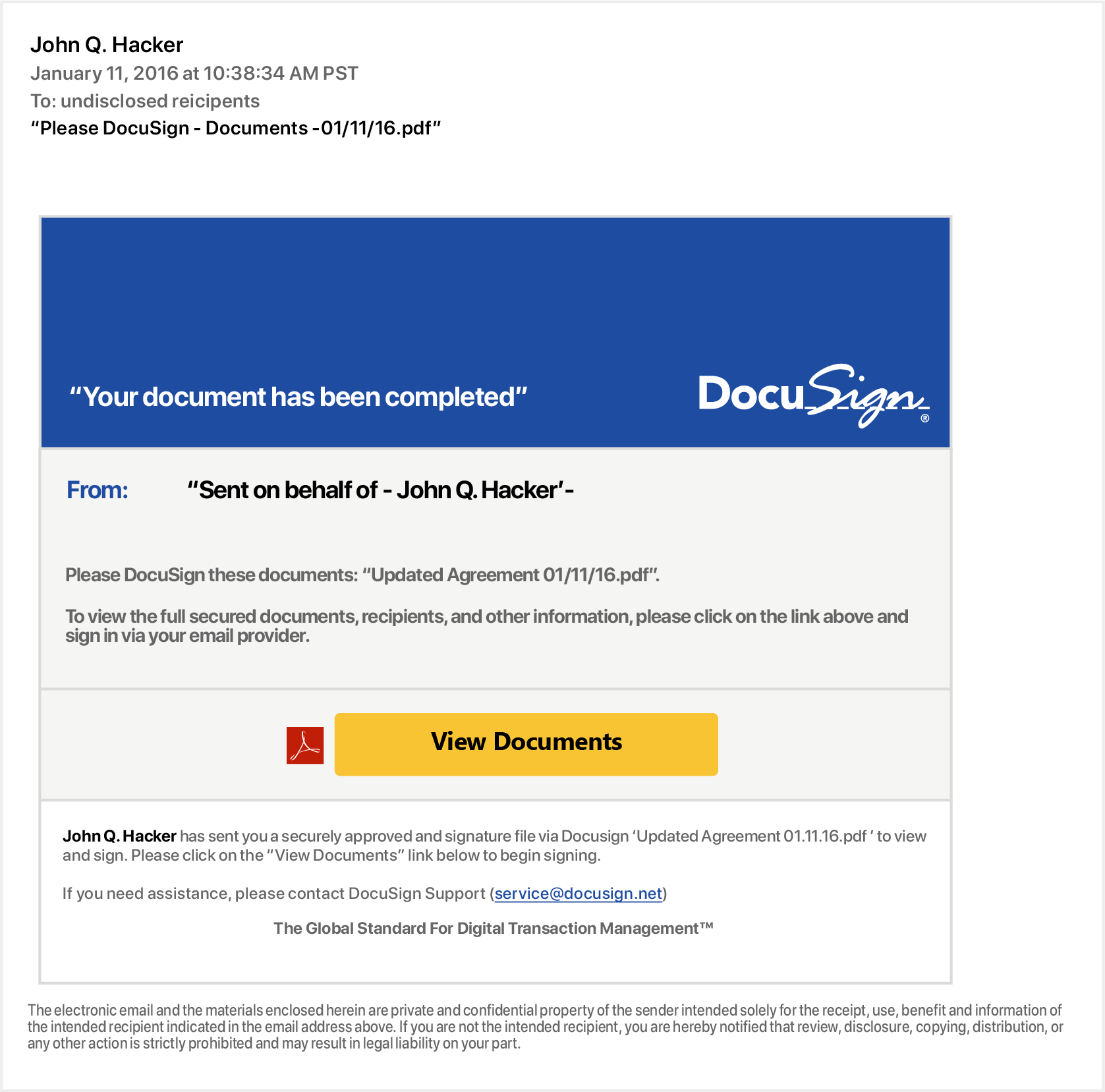
Phishing incident report template. At this point we dont believe that the compromised credentials were used for anything other than to send the phishing email above. The inbound action also creates an email search to locate other email attachments that may be related to the user reported phishing attack. February 19 2016 in pragmatic news by david lockie. Report a cyber incident.
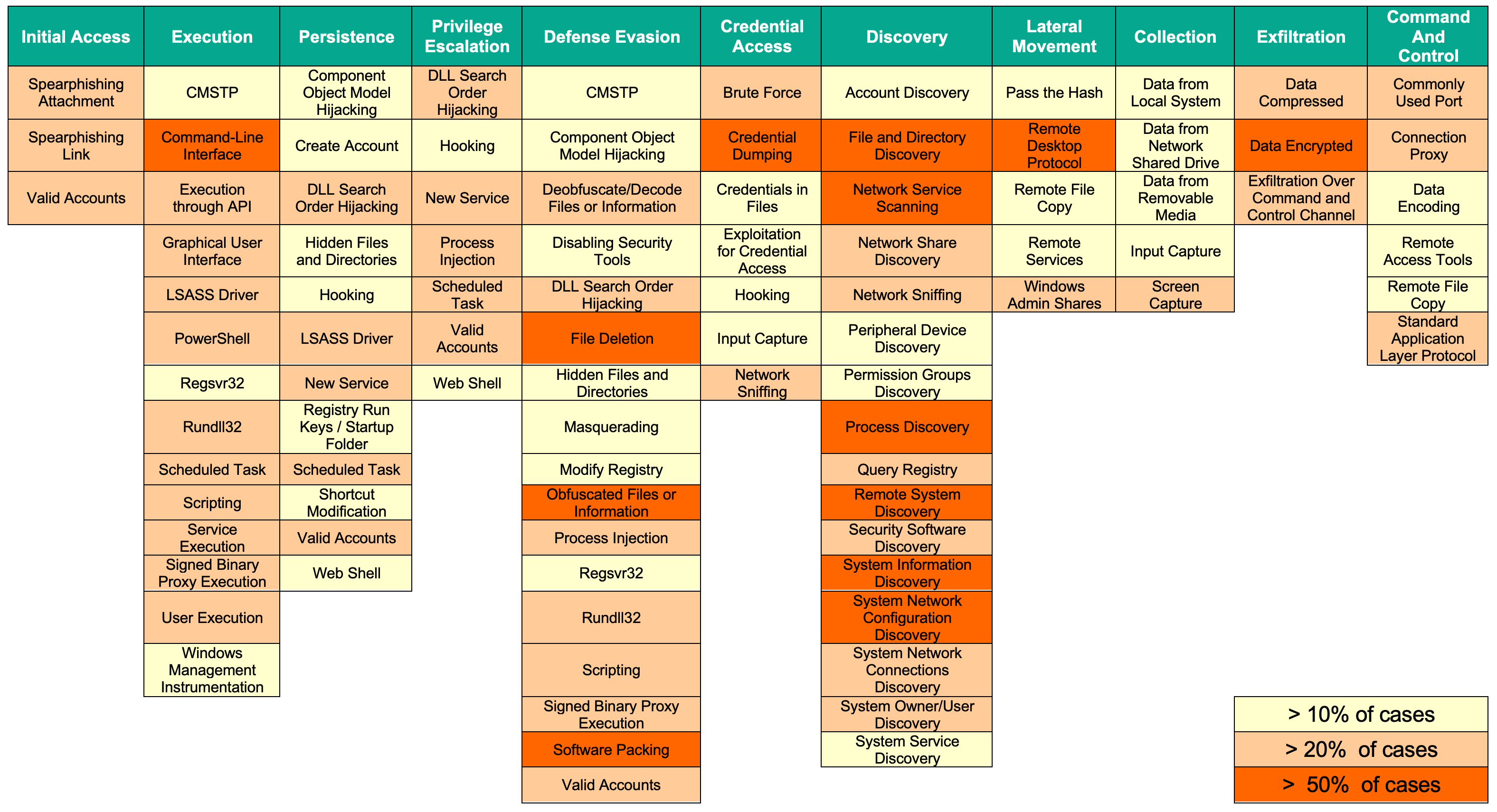
Her google account doesnt give her access to any. Prepare detect analyze contain eradicate recover post incident handling. Building a kill chain. Try smartsheet for free.
The email search is associated with the security incident and searches for other eml records that have the same subject and are from the same sender. This is a phishing incident response playbook for dealing with phishing campaign. Failure to file incident reports can sometimes lead to costly fines and penalties. Cisa provides secure means for constituents and partners to report incidents phishing attempts malware and vulnerabilities.
The attackers had access to their account for less than 30 minutes. In this article weve gathered the best incident report templates to provide you with the most comprehensive listing so you can record and preserve key details of an accident injury workplace incident security breach or any other type of unforeseen event. For example today web browsers such as internet explorer mozilla firefox. Free incident report templates.
Send the template to our internal pr on communications. The workflow is triggered when the category in a security incident is set to spear phishing. To submit a report please select the appropriate method from below. Examples of incident reports can be downloaded below for your convenience so that you are able to save time and avoid penaltiesyou may also see consulting report examples incident report template.
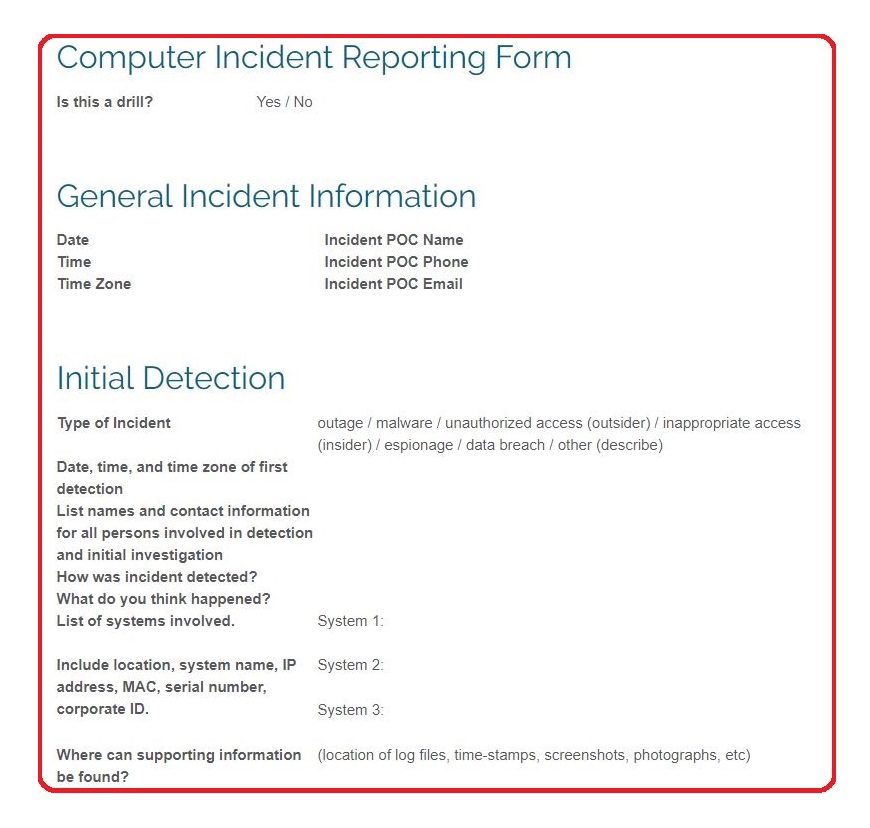
Report incidents as defined by nist special publication 800 61 rev 2 to. Every computer and internet user can play an important role in creating a safe secure cyber environment. It contains the incident response procedures useful in dealing with a phishing campaign. This action causes a response task to be created.
Report a cyber incident. The phishing incident response playbook contains all 7 steps defined by the nist incident response process. Report a phishing incident.