Audit Log Review Template

Here you will learn best practices for leveraging logs.
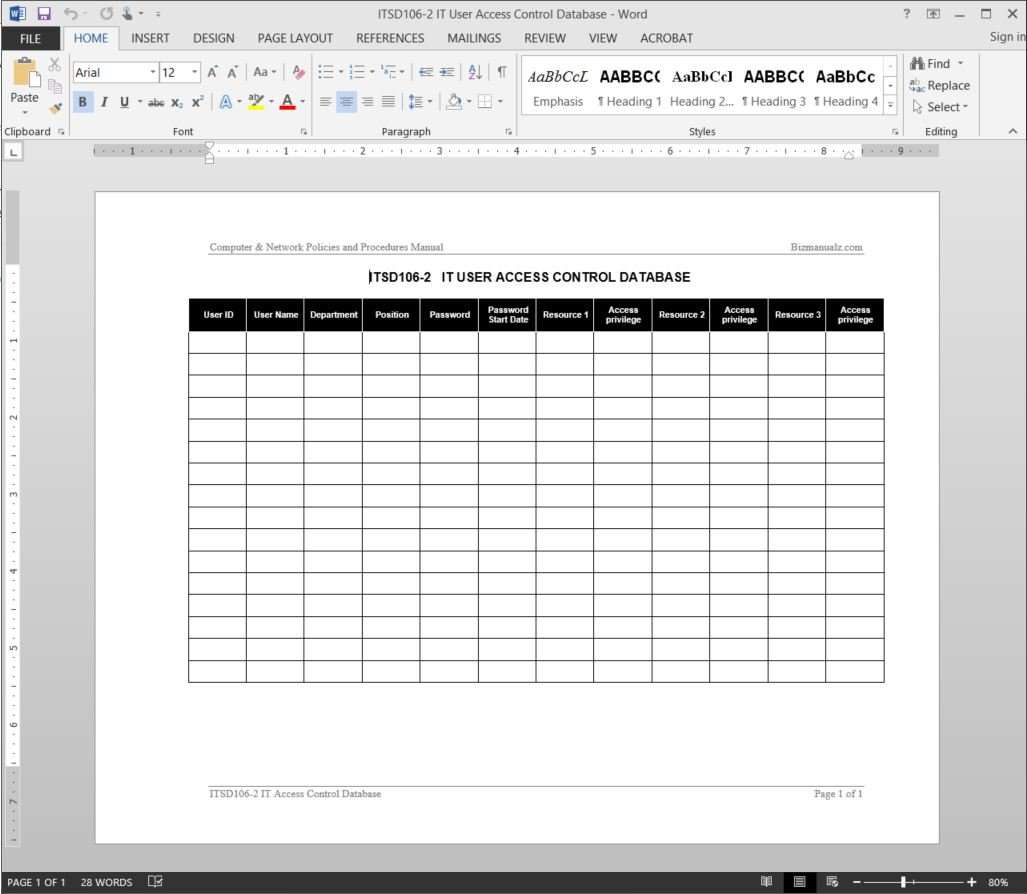
Audit log review template. Log review will be the goal keeper and frequency is critical. Want to implement. This template may also be used as a base for creating your own customized reports on top of your audit data. Internal audit report 200812.
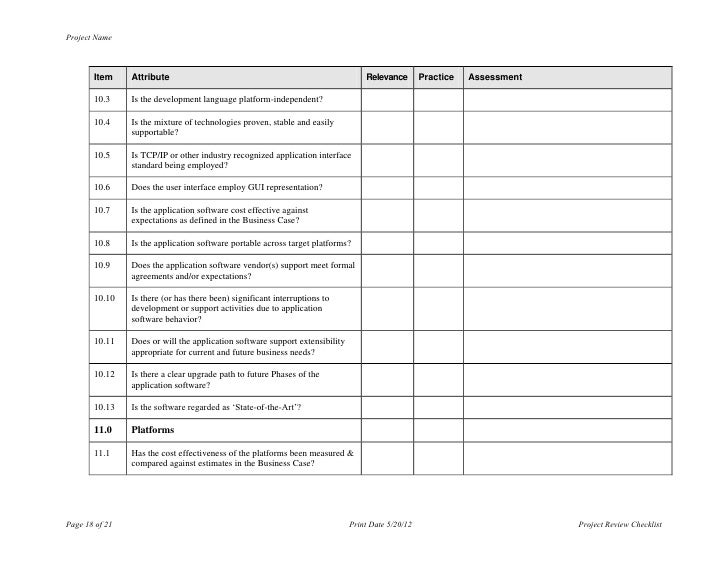
This policy outlines the requirements for audit logging and review with the intent of identifying user and system activity in order to reduce the risk of unauthorized access. The review of membership was undertaken as part of the governance section of the 20082009 internal audit operational plan. The audits performed assess entity compliance with selected requirements and may vary based on the type of covered entity or business associate selected for review. Critical log review checklist for security incidents this cheat sheet presents a checklist for reviewing critical logs when responding to a security incident.
The trusts terms of authorisation state the trust shall continue to take such reasonable steps as may be required by monitor to secure that the actual. In fact log review is a kind of detective control and the preventive control is lacking. In addition a specification detailing the audit log data is available for both table and blob auditing. The audit protocol is organized by rule and regulatory provision and addresses separately the elements of privacy security and breach notification.
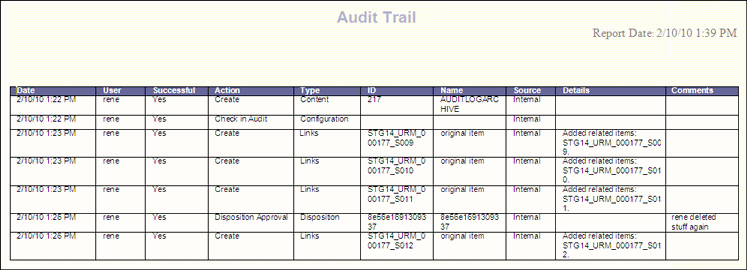
Resource custodians must maintain monitor and analyze security audit logs for covered devices. Audit logging and review are essential in ensuring a diligent and proactive information security and systems environment. Audit logs data can be loaded into the excel file using the power query for excel add in. It can also be used for routine log review.
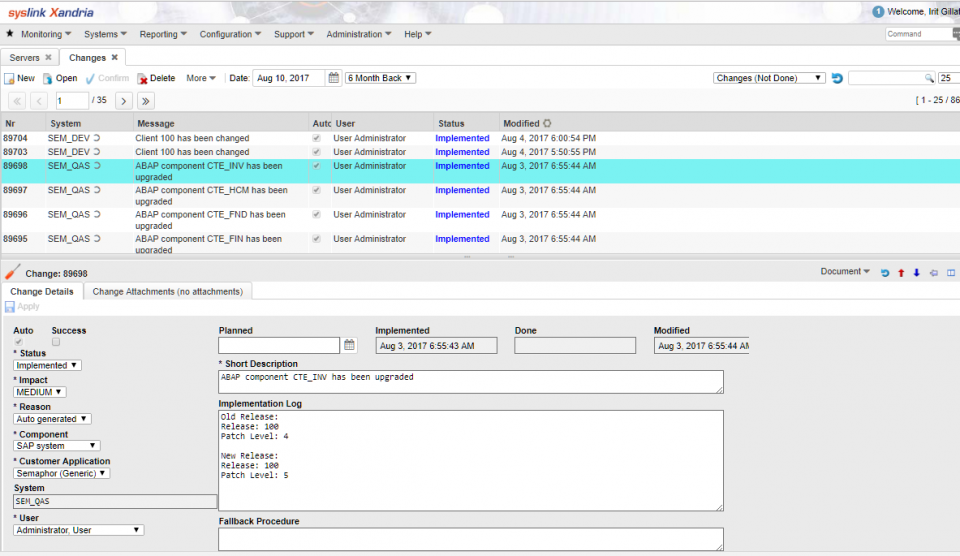
Computer and system logging policy. Damage or circumvent access control and audit log mechanisms. Many organizations keep audit records for compliance purposes but attackers rely on the fact that such organizations rarely look at the audit logs and they do not know that their systems have been compromised. Sample it security policies.
Ensure that appropriate logs are being aggregated to a central log management system for analysis and review. They provide a primary mechanism for automated tracking and reporting for review audit and compliance functions as well as a useful mechanism for tracking changes and troubleshooting. When it comes to it security investigations regular audit log review and monitoring make getting to the root of a breach possible.